In today’s times, Information and Data security is one of the main concerns for all organizations, including those that outsource key business operations to third-party vendors (e.g., SaaS, cloud-computing providers, outsourcing key activities etc.). If misused data by application and network security providers can leave enterprises vulnerable to attacks, such as data theft, blackmail, and malware installation.
SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a vendor.
What is SOC 2
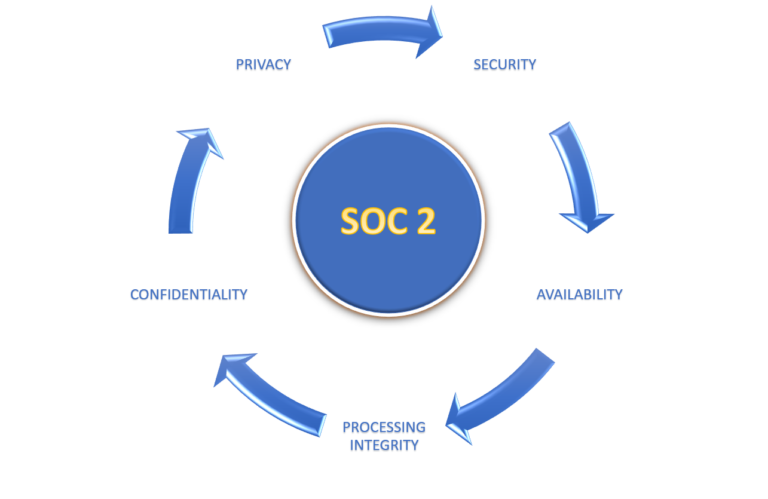 Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 defines criteria for managing customer data based on five “trust service principles”—security, availability, processing integrity, confidentiality, and privacy.
Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 defines criteria for managing customer data based on five “trust service principles”—security, availability, processing integrity, confidentiality, and privacy.
There are two types of SOC reports:
Type I: describes a vendor’s systems and whether their design is suitable to meet relevant trust principles.
Type II: details the operational effectiveness of those systems.
How PBC can support
Principle Business Consultants is one of the leading SOC2 Consultants in Kerala, India. We offer comprehensive solutions tailored to meet your organization’s specific needs. With a deep understanding of security, availability, processing integrity, confidentiality, and privacy, we guide you through the intricacies of SOC2 compliance. Our expert consultants employ a systematic approach, conducting thorough assessments, identifying gaps, and implementing robust controls to fortify your systems and processes. We prioritize transparency, reliability, and confidentiality throughout the engagement, ensuring compliance with industry standards and regulatory requirements. With PBC’s SOC2 consulting services, you gain peace of mind knowing that your organization is equipped to safeguard sensitive data and uphold trust with stakeholders.

